Fintech Startup Offers $500 for Payroll Passwords
lundi 10 mai 2021 à 16:25How much is your payroll data worth? Probably a lot more than you think. One financial startup that’s targeting the gig worker market is offering up to $500 to anyone willing to hand over the payroll account username and password given to them by their employer, plus a regular payment for each month afterwards in which those credentials still work.

This ad, from workplaceunited[.]com, promised up to $500 for people who provided their payroll passwords, plus $25 a month for each month those credentials kept working.
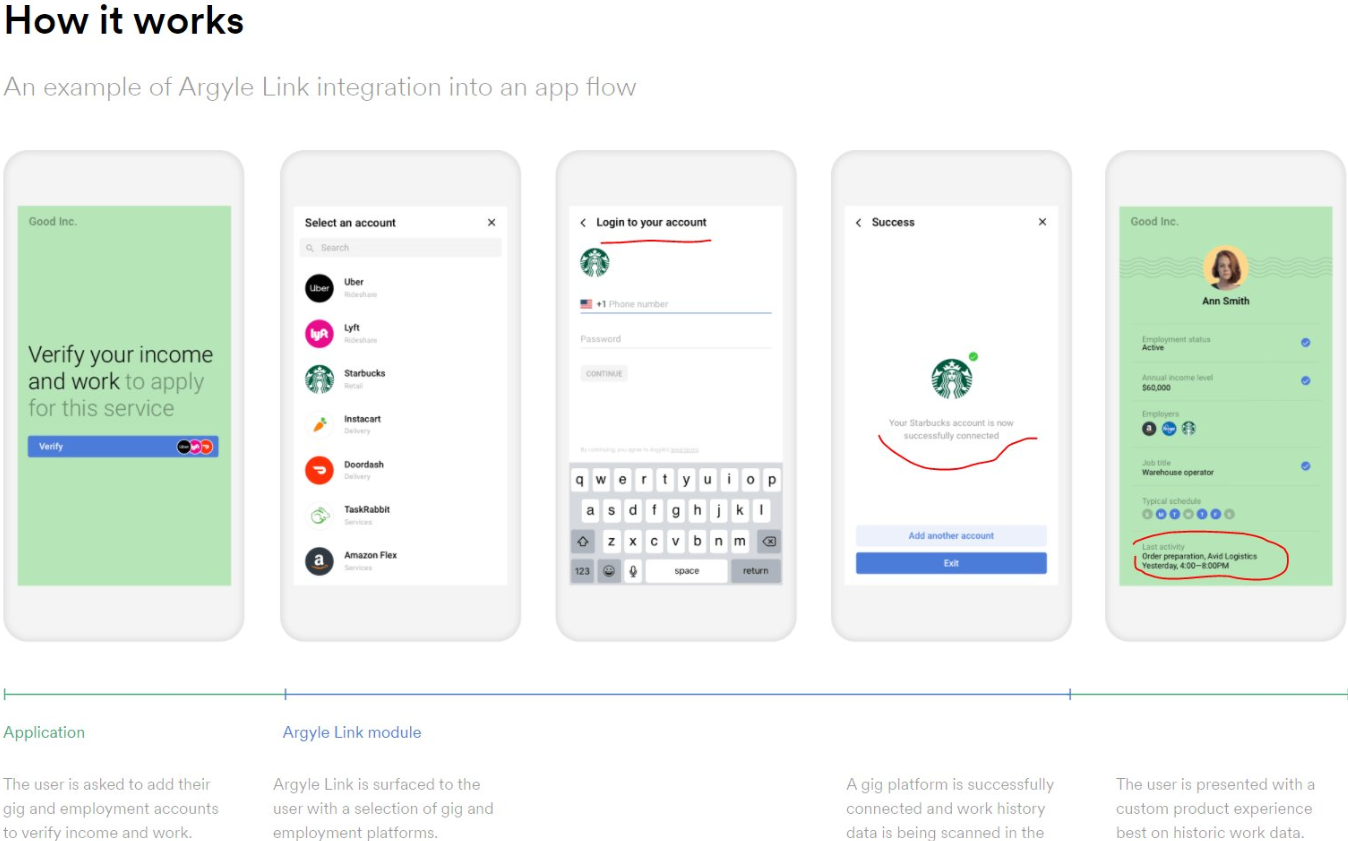
New York-based Argyle.com says it’s building a platform where people who work multiple jobs and/or side hustles can improve their credit and employment options by pooling all of their gig work data in one place.
“Consumers’ access to financial security and upward mobility is dependent on their access to and control over their own employment records and how easily they can share those records with financial institutions,” Argyle explained in a May 3 blog post. “We enable access to a dataset that, for too long, has gone unstandardized, unregulated, and controlled by corporations instead of consumers, contributing to system-wide inequalities.”
In that sense, Argyle is making a play for a discrete chunk of a much larger employment data market dominated by the major credit bureaus, which have been hoovering up and selling access to employment data for years.
The 800-lb. gorilla there is Equifax, whose The Work Number product has for years purchased employment data flows from some of the world’s largest companies (employees consent to this sharing as part of their employment contract, and The Work Number makes it fairly easy for anyone to learn how much you earn).
The Work Number is designed to provide automated employment and income verification for prospective employers, and tens of thousands of companies report employee salary data to it. It also allows anyone whose employer uses the service to provide proof of their income when purchasing a home or applying for a loan.
On its blog, Argyle imagines a world in which companies choose to integrate its application platform interface (API) and share their employee payroll data. At the same time, the company appears to be part of an effort in which non-salaried workers are prompted to repay their erstwhile employers’ trust by selling payroll credentials.
If Argyle is worried these two goals might somehow conflict, that is not obvious by looking at some of its direct-to-consumer efforts.
The website pictured below prompts visitors to “connect payroll,” and those who proceed agree to have their payroll data shared with a company called Earnin, a mobile payday loan app that lets users get an advance on their upcoming paycheck.

Clicking “Connect Payroll” brings up a list of payroll login pages for brand name companies, including Walmart, Starbucks, Amazon, Uber, Chipotle, etc., with a search feature that reveals login pages for everyone from the Federal Bureau of Investigation (FBI) to the Federal Reserve and Federal Trade Commission (FTC).

The default Argyle list of payroll login pages for major companies.
Here’s what comes up when you search by “Department of” at this site:

Drilling down into individual companies listed here produces a username and password form that in some cases is modified to request an employee identifier other than a username, such as a employee ID, associate or partner number instead. Here’s the login page for Starbucks employees:

The site pictured above actively checks if any submitted credentials are working, by submitting them directly to the employer in question. This Argyle status page indicates the system’s “data connection status” to countless employers.
Some of you may be thinking, “How many of us actually know or have our payroll passwords?” According to Argyle, plenty of people do.
“At Argyle, we are intimately familiar with how likely someone is to know the password for their employment account or payroll system, because we’ve seen hundreds of thousands of users successfully (and unsuccessfully) provide their credentials,” Argyle’s Billy Mardsen wrote on Apr. 1. “We closely monitor their success rate—what we call conversion—because it drives the performance of the products and applications that our clients build on top of Argyle.”

Argyle’s “conversion” numbers by employer. Image: Argyle.com
UNCOMMON GROUNDS
KrebsOnSecurity first heard about this company via Twitter from security researcher Kevin Beaumont, who pointed to a nest of domains associated with Argyle’s API — nearly all of which are offline now. At the time, Beaumont and others digging into this suspected the sites were part of an elaborate phishing scam.
These sites, which seemed to be grouped around a recent recruitment effort variously called “Workers United,” “UniteAtWork,” “WageCompete” and “CommonGrounds,” indicate that Argyle’s platform has been pivotal in a slew of campaigns paying employees at specific companies up to $100 for their payroll account passwords. Here’s one seeking T-Mobile employees:

A promotion offering T-Mobile employees $100 to give up their T-Mobile payroll account passwords.
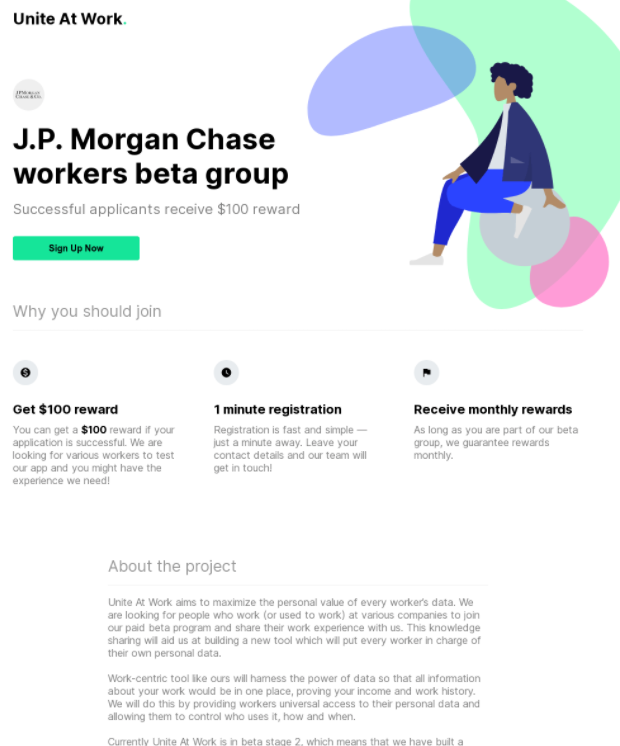
Another recent promotion targeted employees at J.P. Morgan Chase, the largest financial institution in the United States:
Argyle declined multiple interview requests for this story, so it’s not clear how much of a role — if any — the company may have played in these various sites. But code prebuilds and instructions published in the company’s name on Github strongly suggest Argyle was instrumental in the WageCompete initiative.
Also, this page over at Scopeinc.com says the WageCompete program is provided by Argyle Expert Services.
Here’s a graphical look at the various websites mentioned here and their ties to Argyle’s API (click to enlarge):

The network of sites paying people for payroll passwords and their connections to Argyle’s API. Click to enlarge. Image: Virustotal
One of the sites in that graphic above that’s connected to Argyle’s API — workerresearchalliances[.]com — is currently live and includes the same verbiage about participants getting paid for their payroll credentials. The terms and conditions of the “WorkersApp beta program” were set by a company called Workers Research Alliances LLC, incorporated in February. The address for Workers Research Alliances is just a few blocks from Argyle’s office in New York City.
‘WE DO THINGS OTHERS DARE NOT DO’
Steve Friedl, an IT consultant in the payroll service bureau industry, said it appears Argyle has been paying people to help them refine their API and data scraping technology.
“They are not paying this money just to be able to sell people services, they are doing so to maintain their screen-scraping software API,” Friedl said. “This is essentially paying employees to help Argyle hack their payroll provider.”
Last fall Argyle announced it had landed a $20 million investment from Bain Capital, among others. The company’s co-founder, Shmulik Fishman, is described as a “disruptor” who says he wants to make credit scores obsolete.
“We’re fearless,” Fishman told Authority Magazine. “We do things other people dare not do.”
That much is clear. Hey, I can get behind almost anything that disintermediates the creaky old credit bureaus in a straightforward and consumer-friendly way. And the last time I checked, it’s not against the law to give someone your password, or to induce someone to do so willingly in exchange for something else (unless maybe you work for a federal agency).
But I wonder how many of the companies listed on all these payroll connect sites will respond to knowing their brands and logos are associated with a site that asks their employees to give away passwords.
KrebsOnSecurity contacted multiple high-level sources at major companies whose login pages are shown in these payroll connect programs running on Argyle’s platform. None of those sources were authorized to talk to the media, but all seemed fairly horrified at what they were seeing, and each said their employer’s legal departments were launching their own investigations.
Beaumont said he’s worried that in some companies, an employee’s payroll credentials may work to gain access to other parts of the organization — meaning some employees may be giving away more than they realize.
“My concern is some companies use single sign-on for payroll,” Beaumont said. “That’s a lot of access for a data harvesting company.”