Four Men Charged With Hacking 500M Yahoo Accounts
jeudi 16 mars 2017 à 01:49“Between two evils, I always pick the one I never tried before.” -Karim Baratov (paraphrasing Mae West)
The U.S. Justice Department today unsealed indictments against four men accused of hacking into a half-billion Yahoo email accounts. Two of the men named in the indictments worked for a unit of the Russian Federal Security Service (FSB) that serves as the FBI’s point of contact in Moscow on cybercrime cases. Here’s a look at the accused, starting with a 22-year-old who apparently did not try to hide his tracks.
According to a press release put out by the Justice Department, among those indicted was Karim Baratov (a.k.a. Kay, Karim Taloverov), a Canadian and Kazakh national who lives in Canada. Baratov is accused of being hired by the two FSB officer defendants in this case — Dmitry Dokuchaev, 33, and Igor Sushchin, 43 — to hack into the email accounts of thousands of individuals.
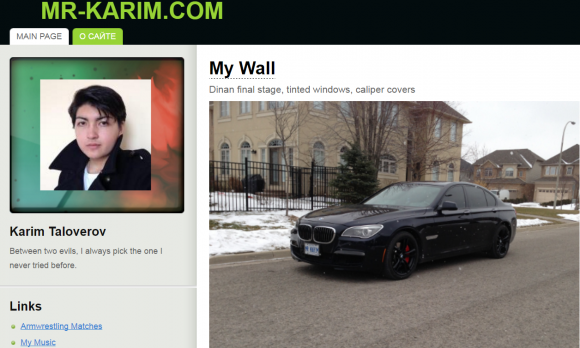
Karim Baratov (a.k.a. Karim Taloverov), as pictured in 2014 on his own site, mr-karim.com. The license plate on his BMW pictured here is Mr. Karim.
Reading the Justice Department’s indictment, it would seem that Baratov was perhaps the least deeply involved in this alleged conspiracy. That may turn out to be true, but he also appears to have been the least careful about hiding his activities, leaving quite a long trail of email hacking services that took about 10 minutes of searching online to trace back to him specifically.
Security professionals are fond of saying that any system is only as secure as its weakest link. It would not be at all surprising if Baratov was the weakest link in this conspiracy chain.
A look at Mr. Baratov’s Facebook and Instagram photos indicates he is heavily into high-performance sports cars. His profile picture shows two of his prized cars — a Mercedes (pictured above) and an Aston Martin — parked in the driveway of his single-family home in Ontario.
A simple reverse WHOIS search at domaintools.com on the name Karim Baratov turns up 81 domains registered to someone by this name in Ontario. Many of those domains include the names of big email providers like Google and Yandex, such as accounts-google[dot]net and www-yandex[dot]com.
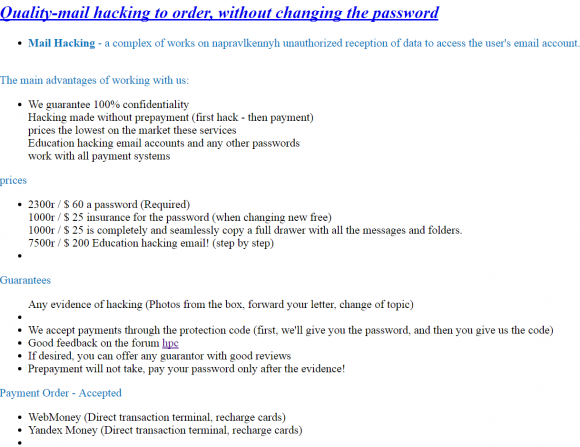
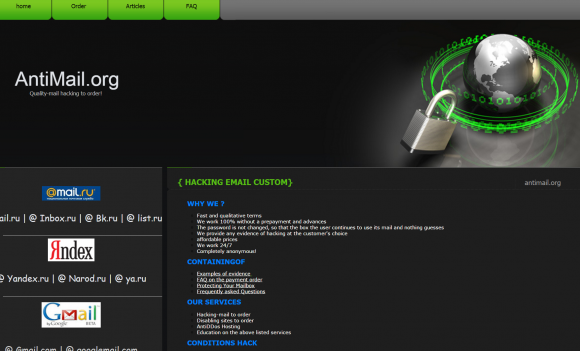
Other domains appear to be Web sites selling email hacking services. One of those is a domain registered to Baratov’s home address in Ancaster, Ontario called infotech-team[dot]com. A cached copy of that site from archive.org shows this once was a service that offered “quality mail hacking to order, without changing the password.” The service charged roughly $60 per password.
The proprietors of Infotech-team[dot]com advertise the ability to steal email account passwords without actually changing the victim’s password. According to the Justice Department, Baratov’s service relied on “spear phishing” emails that targeted individuals with custom content and enticed the recipient into clicking a link.
Antimail[dot]org is another domain registered to Baratov that was active between 2013 and 2015. It advertises “quality-mail hacking to order!”:
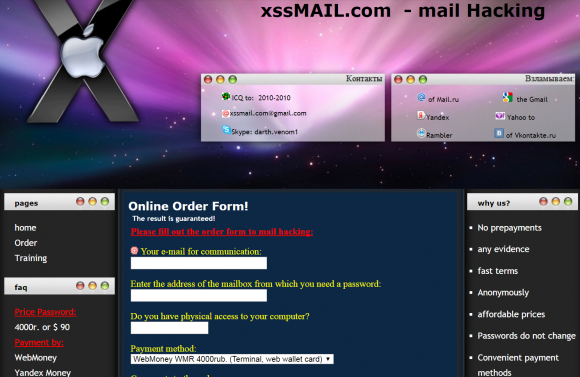
Another email hacking business registered to Baratov is xssmail[dot]com, which also has for several years advertised the ability to break into email accounts of virtually all of the major Webmail providers. XSS is short for “cross-site-scripting.” XSS attacks rely on vulnerabilities in Web sites that don’t properly parse data submitted by visitors in things like search forms or anyplace one might enter data on a Web site.
In the context of phishing links, the user clicks the link and is actually taken to the domain he or she thinks she is visiting (e.g., yahoo.com) but the vulnerability allows the attacker to inject malicious code into the page that the victim is visiting.
This can include fake login prompts that send any data the victim submits directly to the attacker. Alternatively, it could allow the attacker to steal “cookies,” text files that many sites place on visitors’ computers to validate whether they have visited the site previously, as well as if they have authenticated to the site already.
Perhaps instead of or in addition to using XSS attacks in targeted phishing emails, Baratov also knew about or had access to other cookie-stealing exploits collected by another accused in today’s indictments: Russian national Alexsey Alexseyevich Belan.
According to government investigators, Belan has been on the FBI’s Cyber Most Wanted list since 2013 after breaking into and stealing credit card data from a number of e-commerce companies. In June 2013, Belan was arrested in a European country on request from the United States, but the FBI says he was able to escape to Russia before he could be extradited to the U.S.
The government says the two other Russian nationals who were allegedly part of the conspiracy to hack Yahoo — the aforementioned FSB Officers Dokuchaev and Sushchin — used Belan to gain unauthorized access to Yahoo’s network. Here’s what happened next, according to the indictments:
“In or around November and December 2014, Belan stole a copy of at least a portion of Yahoo’s User Database (UDB), a Yahoo trade secret that contained, among other data, subscriber information including users’ names, recovery email accounts, phone numbers and certain information required to manually create, or ‘mint,’ account authentication web browser ‘cookies’ for more than 500 million Yahoo accounts.
“Belan also obtained unauthorized access on behalf of the FSB conspirators to Yahoo’s Account Management Tool (AMT), which was a proprietary means by which Yahoo made and logged changes to user accounts. Belan, Dokuchaev and Sushchin then used the stolen UDB copy and AMT access to locate Yahoo email accounts of interest and to mint cookies for those accounts, enabling the co-conspirators to access at least 6,500 such accounts without authorization.”
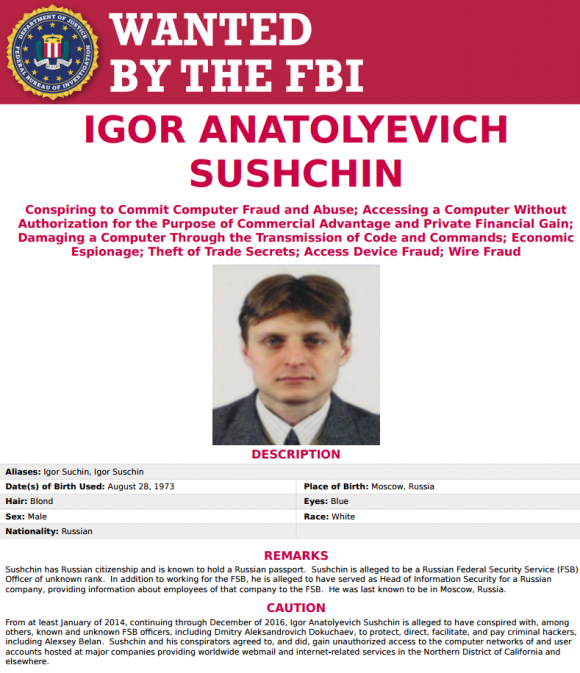
U.S. investigators say Dokuchaev was an FSB officer assigned to Second Division of FSB Center 18, also known as the FSB Center for Information Security. Dokuchaev’s colleague Sushchin was an associate of FSB officer was embedded as a purported employee and Head of Information Security at a Russian financial firm, where he monitored the communications of the firm’s employees.
According to the Justice Department, some victim accounts that Dokuchaev and Sushchin asked Belan and Baratov to hack were of predictable interest to the FSB (a foreign intelligence and law enforcement service), such as personal accounts belonging to Russian journalists; Russian and U.S. government officials; employees of a prominent Russian cybersecurity company; and numerous employees of other providers whose networks the conspirators sought to exploit. Other personal accounts belonged to employees of commercial entities, such as a Russian investment banking firm, a French transportation company, U.S. financial services and private equity firms, a Swiss bitcoin wallet and banking firm and a U.S. airline.
“During the conspiracy, the FSB officers facilitated Belan’s other criminal activities, by providing him with sensitive FSB law enforcement and intelligence information that would have helped him avoid detection by U.S. and other law enforcement agencies outside Russia, including information regarding FSB investigations of computer hacking and FSB techniques for identifying criminal hackers,” the Justice Department charged in its press statement about the indictments.
“Additionally, while working with his FSB conspirators to compromise Yahoo’s network and its users, Belan used his access to steal financial information such as gift card and credit card numbers from webmail accounts; to gain access to more than 30 million accounts whose contacts were then stolen to facilitate a spam campaign; and to earn commissions from fraudulently redirecting a subset of Yahoo’s search engine traffic,” the government alleges.
Each of the four men face 47 criminal charges, including conspiracy, computer fraud, economic espionage, theft of trade secrets and aggravated identity theft.
Dokuchaev, who is alleged to have used the hacker nickname “Forb,” was arrested in December in Moscow. According to a report by the Russian news agency Interfax, Dokuchaev was arrested on charges of treason for alleging sharing information with the U.S. Central Intelligence Agency (CIA). For more on that treason case, see my Jan. 28, 2017 story, A Shakeup in Russia’s Top Cybercrime Unit.
For more on Dokuchaev’s allegedly checkered past (Russian news sites report that he went to work for the FSB to avoid being prosecuted for bank fraud) check out this fascinating story from Russian news outlet Vedomosti, which featured interview with the hacker Forb from 2004.
In September 2016, Yahoo first disclosed the theft of 500 million accounts that is being attributed to this conspiracy. But in December 2016, Yahoo acknowledged that a separate hack from 2013 that it attributed to a “state-sponsored actor” had jeopardized more than a billion user accounts.
The New York Times reports that Yahoo said it has not been able to glean much information about that attack, which was uncovered by InfoArmor, an Arizona security firm. Interestingly, that attack also involved the use of forged Yahoo cookies, according to a statement from Yahoo’s chief information security officer.
The one alleged member of this conspiracy who would have been simple to catch is Baratov, as he does not appear to have hidden his wealth and practically peppers the Internet with pictures of six-digit sports cars he has owned over the years.
Baratov was arrested on Tuesday in Canada, where the matter is now pending with Canadian authorities. U.S. prosecutors are now trying to seize Baratov’s black Mercedes Benz C54 and his Aston Martin DBS, arguing that they were purchased with the proceeds from cybercrime activity.
A redacted copy of the indictment is available here.


 Microsoft’s
Microsoft’s  The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out
The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out 


 On March 5, a security researcher named Bashis posted to
On March 5, a security researcher named Bashis posted to