With little more than a month to go before the start of the 2016 tax filing season, the IRS and the states are hunkering down for an expected slugfest with identity thieves who make a living requesting fraudulent tax refunds on behalf of victims. Here’s what you need to know going into January to protect you and your family.
 The good news is that the states and Uncle Sam have got a whole new bag of technological tricks up their sleeves this coming tax season. The bad news is ID thieves are already testing those defenses, and will be working against a financially strapped federal agency that’s been forced to cede much of its ability to investigate and prosecute such crimes.
The good news is that the states and Uncle Sam have got a whole new bag of technological tricks up their sleeves this coming tax season. The bad news is ID thieves are already testing those defenses, and will be working against a financially strapped federal agency that’s been forced to cede much of its ability to investigate and prosecute such crimes.
Tax refund fraud affects hundreds of thousands, if not millions, of U.S. citizens annually. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually due a refund from the IRS.
By all accounts, the IRS has improved at blocking phony refund requests. The agency estimates it prevented $24.2 billion in fraudulent identity theft refunds in 2013. Trouble is, it paid out some $5.8 billion in fraudulent refunds that year that it later determined were bogus, and experts say that is only the fraud the agency knows about, and the true number is likely much higher annually.
Perhaps in response to the IRS’s increasing ability to separate phony returns from legitimate ones, crooks last year massively focused on filing bogus refund requests with the 50 U.S states. To head off a recurrence of that trend in the 2016 filing season, the states and the IRS have hammered out an agreement to examine more than 20 new data elements collected by online providers like TurboTax and H&R Block.
Those new data elements include checking for the repetitive use of the same Internet address to rapidly file multiple returns, and reviewing computer device information (browser user agent string, cookies e.g.) tied to the return’s origin. Another check involves measuring the time it takes to file a return; fraudsters involved in tax refund fraud tend to breeze through returns in just a few minutes because they are generally copying and pasting information into the tax forms, or relying on an automated program to do it for them.
The hope is that the these new checks will let investigators more accurately flag suspicious refund requests processed by tax preparation firms, which also have agreed to beef up lax security around customer accounts. Under the agreement, online providers will enforce:
- new password standards to include a minimum of eight characters, with upper, lowercase, alphanumerical and special characters;
- a lock-out feature that blocks users with too many unsuccessful login attempts;
- the addition of three security questions;
- some sort of out-of-band verification for email addresses — sending an email or text to the customer with a personal identification number (PIN).
Julie Magee, Alabama’s chief tax administrator, said the state/IRS task force opted not to disclose all 20 of the data elements they will be collecting from tax prep firms.
“The thieves are going to figure these out on their own, and they’re already testing our defenses,” Magee told KrebsOnSecurity. “We don’t want to do anything to make that easier for them.”
ANALYSIS
Whether or not we see an increase in tax refund fraud next year, one thing seems certain: the IRS will prosecute far fewer of the crooks involved. Congress has persistently underfunded the IRS, and budget cuts have pushed prosecutions of identity thieves to a new low. According to the IRS’s 2015 Annual Report, IRS identity theft criminal investigations are down almost 50 percent since 2013.
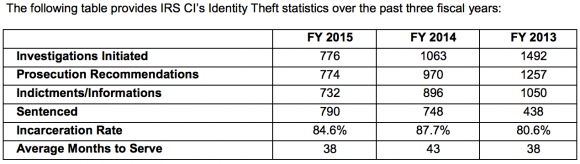
Tax fraudsters were so aggressive last year that they figured out how to steal consumer identities directly from the agency itself. In August 2015, the IRS disclosed that crooks abused the “Get Transcript” feature on its Web site to steal Social Security numbers and information from previous years’ tax filings on more than 334,000 Americans.
The IRS has responded to the problem of tax ID theft partly by offering Identity Protection PINs (IP PINs) to affected taxpayers that must be supplied on the following year’s tax application before the IRS will accept the return. However, consumers still have to request an IP PIN by applying for one at the agency’s site, or by mailing in form 14039 (PDF).
Incredibly, the process that thieves abused to steal tax transcripts from 334,000 taxpayers this year from the IRS’s site also works to fraudulently obtain a consumer’s IP PIN. In fact, the following redacted screen shot from a notorious cybercrime forum shows a seasoned tax fraudster teaching would-be scammers how to use the IRS’s site to obtain a victim’s IP PIN.
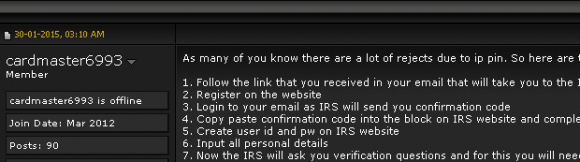
Both the Get Transcript and the process to retrieve an IP PIN from the IRS’s site are vulnerable because they rely on the applicant supplying static information that is trivial for thieves to obtain, including the taxpayer’s name, date of birth, Social Security number and filing status. After that data is successfully supplied, the IRS uses a service from credit bureau Equifax that asks four so-called “knowledge-based authentication” (KBA) questions.
These KBA questions — which involve multiple choice, “out of wallet” questions such as previous address, loan amounts and dates — can be successfully enumerated with random guessing, but much of the data is readily available via free online social networking and consumer tracking services like Spokeo.
If any readers here doubt how easy it is to buy personal data on just about anyone, check out the story I wrote in December 2014, wherein I was able to find the name, address, Social Security number, previous address and phone number on all current members of the U.S. Senate Commerce Committee. This information is no longer secret (nor are the answers to KBA-based questions), and we are all made vulnerable to identity theft as long as institutions continue to rely on static information as authenticators.
My guess is that a huge chunk of 334,000 victimized via the IRS’s site this year probably will not request the IP PIN and will in fact have fraudulent tax returns filed with their info — whether they request the IP PIN and it is stolen or not. The IRS should just issue the IP PINs to affected taxpayers, instead of asking victims to do it themselves.
Incidentally, the IRS’s Twitter account is still promoting the online Get Transcript capability, even though it no longer offers the service online. For now, the only way to obtain a transcript is via snail mail.

IRS’s Twitter account urging followers to use a service that hasn’t been available since May 2015.
DON’T BE THE NEXT VICTIM
In notifying 334,000 taxpayers affected by its Get Transcript debacle, the IRS predictably offered victims free credit monitoring services from Equifax. The IRS makes no mention of a more effective way to block ID thieves: Placing a “security freeze” on one’s credit files with the major credit bureaus. See this tutorial about why freezes are more effective than credit monitoring in blocking ID thieves from assuming your identity to open up new lines of credit.
While it’s true that having a security freeze on your credit file won’t stop thieves from committing tax refund fraud in your name, it would stop them from fraudulently obtaining your IP PIN. Also, anyone who has a freeze in place will need to temporarily lift that freeze to take advantage of any credit monitoring services (in this case, the consumer would need to briefly thaw a freeze at Equifax).
-File before the fraudsters do it for you – Your primary defense against becoming the next victim is to file your taxes at the state and federal level as quickly as possible after the 2016 Tax Filing Season begins — which is usually the second or third week in January. Remember, it doesn’t matter whether or not the IRS owes you money: Thieves can still try to impersonate you and claim that they do, leaving you to sort out the mess with the IRS later.
-Get on a schedule to request a free copy of your credit report. By law, consumers are entitled to a free copy of their report from each of the major bureaus once a year. Put it on your calendar to request a copy of your file every three to four months, each time from a different credit bureau. Dispute any unauthorized or suspicious activity. This is where credit monitoring services are useful: Part of their service is to help you sort this out with the credit bureaus, so if you’re signed up for credit monitoring make them do the hard work for you.
–Monitor, then freeze. Take advantage of any free credit monitoring available to you, and then freeze your credit file with the four major bureaus. Instructions for doing that are here.
-File form 14039 and request an IP PIN from the government. This form requires consumers to state they believe they’re likely to be victims of identity fraud. Even if thieves haven’t tried to file your taxes for you yet, virtually all Americans have been touched by incidents that could lead to ID theft — even if we just look at breaches announced in the past year alone.
FIGHT BACK
Thieves involved in tax return fraud may be laughing all the way to the bank, but that doesn’t mean we have to suck it up and take it: Exercise your rights to obtain a copy of the phony return, and you may just help put crooks in jail.
If you become of the victim of tax fraud and are motivated to learn who helped to defraud you and Uncle Sam, you can file form 4506 (plus a $50 fee) to get a copy of the return. That information can be shared with your local police, who may be able to use to track down people who help launder the proceeds from tax refund fraud.
Earlier this year, I wrote about Isha Sesay, a Pennsylvania woman who was arrested for receiving phony IRS refunds on behalf of at least two tax fraud victims. Among Sesay’s victims was resident Mike Kasper, whose request for the filing led to Sesay’s arrest. Kasper’s hard work helped expose the IRS’s pervasive authentication weaknesses and later testified to Congress about his ordeal. Sesay is currently scheduled to plead guilty (PDF) to the charges on Dec. 18.
Turns out, Kasper’s sleuthing was key to Sesay’s prosecution. When he found out he’d been victimized, Kasper requested the copy of returns that fraudsters filed in his name, but he did so before filing form 14039 to request an IP PIN. Had he done it in the opposite order, the IRS would have redacted all of Ms. Sesay personal and financial information.

Poughkeepsie, NY victim Michael Kasper testifying before the Senate Homeland Security Committee in June 2015.
In testimony before the Senate this year, IRS Commissioner John Koskinen explained the reasoning behind that decision: A fraudulent return could include the personal information of other people. The end result is that it is better to file form 4506 and pay $50 to request a photocopy of the fraudulent return before you file form 14039 to formally report the fraud.
“There is a section 6103 of the US code that imposes stiff criminal penalties for sharing tax return information and the IRS’s tortured view of reality interprets this law, which is intended to protect personal information, so that once you report fraud and they know some information on the return might not be yours, they believe it is against the law for them to ever share that information with you,” Kasper said.
“As a result, when they recently created the process above for victims to get a copy of the fraudulent tax returns filed in their name, the IRS decided they need to redact any personal info that could possibly belong to a criminal,” Kasper continued. “They do everything they can to protect the privacy of the criminal who already violated your privacy. You actually lose all of your rights once you report the crime so it’s better to wait.”


 IT helpdesk guy by day and security researcher by night, 31-year-old Chris Vickery said he unearthed the 21 gb trove of MacKeeper user data after spending a few bored moments searching for database servers that require no authentication and are open to external connections.
IT helpdesk guy by day and security researcher by night, 31-year-old Chris Vickery said he unearthed the 21 gb trove of MacKeeper user data after spending a few bored moments searching for database servers that require no authentication and are open to external connections. The good news is that the states and Uncle Sam have got a whole new bag of technological tricks up their sleeves this coming tax season. The bad news is ID thieves are already testing those defenses, and will be working against a financially strapped federal agency that’s been forced to cede much of its ability to investigate and prosecute such crimes.
The good news is that the states and Uncle Sam have got a whole new bag of technological tricks up their sleeves this coming tax season. The bad news is ID thieves are already testing those defenses, and will be working against a financially strapped federal agency that’s been forced to cede much of its ability to investigate and prosecute such crimes.



 This type of scam mainly impacts brick-and-mortar retailers that issue gift cards when consumers return merchandise at a store without presenting a receipt. Last week I heard from KrebsOnSecurity reader Lisa who recently went online to purchase a bunch of steeply discounted gift cards issued by pet supply chain Petco.
This type of scam mainly impacts brick-and-mortar retailers that issue gift cards when consumers return merchandise at a store without presenting a receipt. Last week I heard from KrebsOnSecurity reader Lisa who recently went online to purchase a bunch of steeply discounted gift cards issued by pet supply chain Petco.