SSA.GOV To Require Stronger Authentication
mercredi 10 mai 2017 à 15:01The U.S. Social Security Administration will soon require Americans to use stronger authentication when accessing their accounts at ssa.gov. As part of the change, SSA will require all users to enter a username and password in addition to a one-time security code sent their email or phone. In this post, we’ll parse this a bit more and look at some additional security options for SSA users.
The SSA recently updated its portal with the following message:
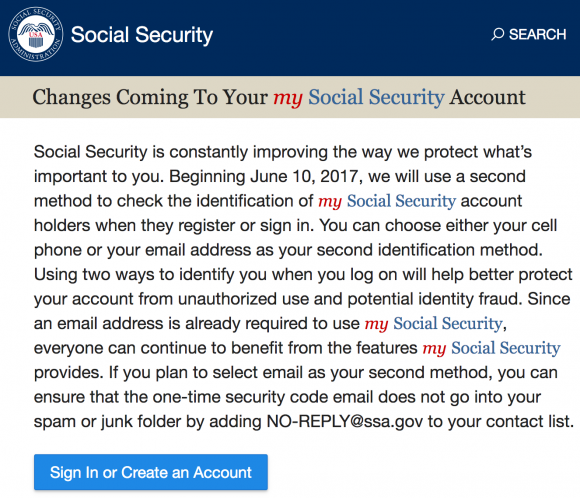
The Social Security Administration’s message to Americans regarding the new login
changes coming in July 2017.
I read that to mean even though an email address is required to sign up at ssa.gov, the SSA also is treating email as a second authentication factor. But the above statement seemed open to interpretation, so I put my questions to the SSA: Here’s what SSA’s press office came back with:
“Beginning June 10, 2017, we will require all my Social Security account holders (both new and returning) to use a stronger authentication method to create an account or access their account. In addition to entering the username and password, people must select either of the following options to receive a one-time use security code:
A text message; or
An email.During registration and each subsequent login, customers will receive a new, one-time use security code by text message or email – depending on their choice.
The combination of the username, password, and one-time use security code will provide access to their personal my Social Security account.”
ANALYSIS
The idea that one can reset the password using the same email account that will receive the one-time code seems to lessen the value of this requirement as a security measure.
Notice the SSA isn’t referring to its new security scheme as “two-factor authentication,” which requires user to supply something he knows and something he is or has.
The former is usually a password or PIN; “something he is” most often refers to biometric components (fingerprint, iris scan); whereas the “something he has” factor generally refers to the output of one-time code from a key-fob or mobile app like Google authenticator or Duo [full disclosure: Duo is a longtime advertiser on this blog].
The move comes almost a year after the SSA enacted and then rescinded a requirement that all Americans who wish to manage their retirement benefits at ssa.gov provide a mobile phone number.
Less than two weeks after that new requirement went into effect last year, the SSA reversed itself and did away with the requirement. The policy was reversed following a rollout marred by technical difficulties and criticism that the new requirement did little to prevent identity thieves from siphoning benefits from Americans who hadn’t yet created accounts at ssa.gov for themselves.
SIGN UP AT SSA BEFORE SOMEONE DOES IT FOR YOU
In September 2013, I warned that SSA and financial institutions were tracking a rise in cases wherein identity thieves register an account at the SSA’s portal using a retiree’s personal information and have the victim’s benefits diverted to prepaid debit cards that the crooks control.
Because it’s possible to create just one my Social Security account per Social Security number, registering an account on the portal is one basic way that Americans can avoid becoming victims of this scam.
So what else beyond the basic measures being enacted in June 2017 does the SSA offer Americans concerned about someone hijacking their SSA account online?
The SSA offers a set of options that it calls “extra security.” These extra options by the way include the sending users a special code via the U.S. Mail that has to be entered on the agency’s site to complete the signup process. If you choose to enable extra security, the SSA will then ask you for:
- The last eight digits of your Visa, MasterCard, or Discover credit card;
- Information from your W2 tax form;
- Information from a 1040 Schedule SE (self-employment) tax form; or
- Your direct deposit amount, if you receive Social Security benefits.
Sadly, crooks won’t go through the more rigorous signup process — they’ll choose the option that requires less information. That means it is still relatively easy for thieves to create an account in the name of Americans who have not already created one for themselves. All one would need is the target’s name, date of birth, Social Security number, residential address, and phone number. This personal data can be bought for roughly $3-$4 from a variety of cybercrime shops online.
What else does the SSA require to prove you’re you when creating a new account at my Social Security? Assuming you can buy or supply the above personal data, the agency relays four multiple-guess, so-called “knowledge-based authentication” or KBA questions from credit bureau Equifax.
In practice, many of these KBA questions — such as previous address, loan amounts and dates — can be successfully enumerated with random guessing. What’s more, very often the answers to these questions can be found by consulting free online services, such as Zillow and Facebook.
In addition to the SSA’s optional security measures, Americans can further block ID thieves by placing a security freeze on their credit files with the major credit bureaus. Readers who have taken my ceaseless advice to freeze their credit will need to temporarily thaw the freeze in order to complete the process of creating an account at ssa.gov.
Looked at another way, having a freeze in place blocks ID thieves from fraudulently creating an account in your name and potentially diverting your government benefits.
Alternatively, citizens can block online access to their Social Security account. Instructions for doing that are here.
 Last week, Google security researcher Tavis Ormandy
Last week, Google security researcher Tavis Ormandy  The latest Flash Player, v. 25.0.0.171 for Windows, Mac, Linux and Chrome OS, is available from
The latest Flash Player, v. 25.0.0.171 for Windows, Mac, Linux and Chrome OS, is available from  A week ago I heard from Troy Mursch, an IT consultant based in Las Vegas. A big fan of proactive medical testing, Mursch said he’s been getting his various lab results reviewed annually for the past two years with the help of a company based in Frisco, Texas called True Health Diagnostics.
A week ago I heard from Troy Mursch, an IT consultant based in Las Vegas. A big fan of proactive medical testing, Mursch said he’s been getting his various lab results reviewed annually for the past two years with the help of a company based in Frisco, Texas called True Health Diagnostics. In
In 