Target Hackers Hit OneStopParking.com
mardi 30 décembre 2014 à 13:54Parking services have taken a beating this year at the hands of hackers bent on stealing credit and debit card data. This week’s victim — onestopparking.com — comes compliments of the same organized crime gang thought to be responsible for stealing tens of millions of card numbers from shoppers at Target and Home Depot.
 Late last week, the cybercrime shop best known for being the first to sell cards stolen in the Target and Home Depot breach moved a new batch of cards taken from an unknown online merchant. Several banks contacted by KrebsOnSecurity acquired cards from this batch, and determined that all had one thing in common: They’d all been used at onestopparking.com, a Florence, Ky. based company that provides low-cost parking services at airport hotels and seaports throughout the United States.
Late last week, the cybercrime shop best known for being the first to sell cards stolen in the Target and Home Depot breach moved a new batch of cards taken from an unknown online merchant. Several banks contacted by KrebsOnSecurity acquired cards from this batch, and determined that all had one thing in common: They’d all been used at onestopparking.com, a Florence, Ky. based company that provides low-cost parking services at airport hotels and seaports throughout the United States.
Contacted about the suspicious activity that banks have traced back to onestopparking.com, Amer Ghanem, the site’s manager, said the company began receiving complaints from customers about a week before Christmas.
“It’s been something we have been dealing with for the past week, where some of our customers have called in and complained about fraudulent charges,” Ghanem said. He noted that the complaints stopped after the company performed several security scans and upgraded software for the Web site, but the investigation continues.
“We have been unable to identify any specific issues that has caused any credit card breach on our website,” Ghanem said in a written statement. “However, being a part of the e-commerce industry and staying up to date with the security news, we are aware of security threats that are always around, especially during the holiday season, when people tend to shop and travel more. We currently have 2 different services that are always monitoring traffic on our website, 24/7 to ensure the safety of our customers.”
This was the second time in as many weeks that this cybercrime shop –Rescator[dot]cm — has put up for sale a batch of credit cards stolen from an online parking service: On Dec. 16, KrebsOnSecurity reported that the same shop was selling cards stolen from Park-n-Fly, a competing airport parking reservation service. Sometime over the past few days, Park-n-Fly announced it was suspending its online service.
“In the wake of suspicious activity relating to certain Park ‘N Fly’s system containing credit card data, Park ‘N Fly has suspended our online reservations system, pending remediation,” reads a security update posted on the company’s site. Park ‘N Fly noted that it is still taking reservations over the phone.
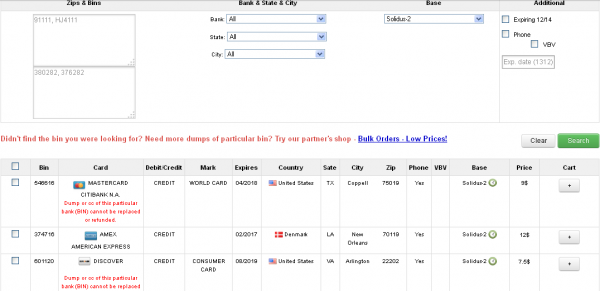
The stolen card data that bank sources traced back to Onestopparking.com are among hundreds or thousands that went on sale Dec. 21 at Rescator, in a batch dubbed “Solidus.” The card data ranges in price from $6 to $12 per card, and include the card number, expiration date, 3-digit card verification code, as well as the cardholder’s name, address and phone number.
Last month, SP Plus — a Chicago-based parking facility provider — said payment systems at 17 parking garages in Chicago, Philadelphia and Seattle that were hacked to capture credit card data after thieves installed malware to access credit card data from a remote location. Card data stolen from those SP+ locations ended up for sale on a competing cybercrime store called Goodshop.
In Missouri, the St. Louis Parking Company recently disclosed that it learned of breach involving card data stolen from its Union Station Parking facility between Oct. 6, 2014 and Oct. 31, 2014.