Ukraine Nabs Suspect in 773M Password ‘Megabreach’
mardi 19 mai 2020 à 18:46In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” A subsequent review by KrebsOnSecurity quickly determined the data was years old and merely a compilation of credentials pilfered from mostly public data breaches. Earlier today, authorities in Ukraine said they’d apprehended a suspect in the case.
The Security Service of Ukraine (SBU) on Tuesday announced the detention of a hacker known as Sanix (a.k.a. “Sanixer“) from the Ivano-Frankivsk region of the country. The SBU said they found on Sanix’s computer records showing he sold databases with “logins and passwords to e-mail boxes, PIN codes for bank cards, e-wallets of cryptocurrencies, PayPal accounts, and information about computers hacked for further use in botnets and for organizing distributed denial-of-service (DDoS) attacks.”

Items SBU authorities seized after raiding Sanix’s residence. Image: SBU.
Sanix became famous last year for posting to hacker forums that he was selling the 87GB password dump, labeled “Collection #1.” Shortly after his sale was first detailed by Troy Hunt, who operates the HaveIBeenPwned breach notification service, KrebsOnSecurity contacted Sanix to find out what all the fuss was about. From that story:
“Sanixer said Collection#1 consists of data pulled from a huge number of hacked sites, and was not exactly his ‘freshest’ offering. Rather, he sort of steered me away from that archive, suggesting that — unlike most of his other wares — Collection #1 was at least 2-3 years old. His other password packages, which he said are not all pictured in the above screen shot and total more than 4 terabytes in size, are less than a year old, Sanixer explained.”
Alex Holden, chief technology officer and founder of Milwaukee-based Hold Security, said Sanixer’s claim to infamy was simply for disclosing the Collection #1 data, which was just one of many credential dumps amalgamated by other cyber criminals.
“Today, it is even a more common occurrence to see mixing new and old breached credentials,” Holden said. “In fact, large aggregations of stolen credentials have been around since 2013-2014. Even the original attempt to sell the Yahoo breach data was a large mix of several previous unrelated breaches. Collection #1 was one of many credentials collections output by various cyber criminals gangs.”
Sanix was far from a criminal mastermind, and left a long trail of clues that made it almost child’s play to trace his hacker aliases to the real-life identity of a young man in Burshtyn, a city located in Ivano-Frankivsk Oblast in western Ukraine.
Still, perhaps Ukraine’s SBU detained Sanix for other reasons in addition to his peddling of Collection 1. According to cyber intelligence firm Intel 471, Sanix has stayed fairly busy selling credentials that would allow customers to remotely access hacked resources at several large organizations. For example, as recently as earlier this month, Intel 471 spotted Sanix selling access to nearly four dozen universities worldwide, and to a compromised VPN account for the government of San Bernadino, Calif.
KrebsOnSecurity is covering Sanix’s detention mainly to close the loop on an incident that received an incredible amount of international attention. But it’s also another excuse to remind readers about the importance of good password hygiene. A core reason so many accounts get compromised is that far too many people have the nasty habit(s) of choosing poor passwords, re-using passwords and email addresses across multiple sites, and not taking advantage of multi-factor authentication options when available.
By far the most important passwords are those protecting our email inbox(es). That’s because in nearly all cases, the person who is in control of that email address can reset the password of any services or accounts tied to that email address – merely by requesting a password reset link via email. For more on this dynamic, please see The Value of a Hacked Email Account.
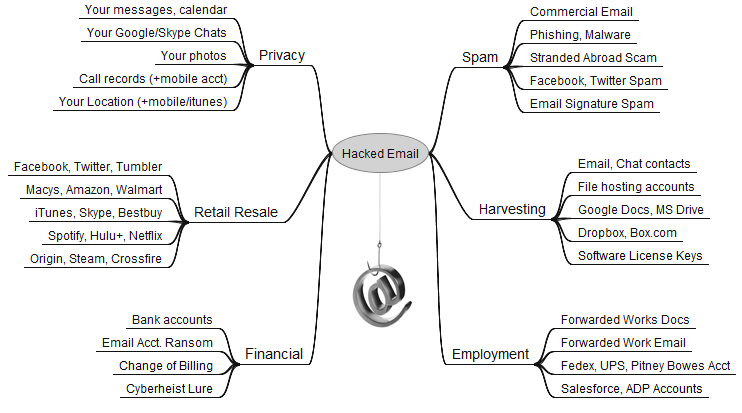
Your email account may be worth far more than you imagine.
And instead of thinking about passwords, consider using unique, lengthy passphrases — collections of words in an order you can remember — when a site allows it. In general, a long, unique passphrase takes far more effort to crack than a short, complex one. Unfortunately, many sites do not let users choose passwords or passphrases that exceed a small number of characters, or they will otherwise allow long passphrases but ignore anything entered after the character limit is reached.
If you are the type of person who likes to re-use passwords, then you definitely need to be using a password manager, which helps you pick and remember strong and unique passwords/passphrases and essentially lets you use the same strong master password/passphrase across all Web sites.
Finally, if you haven’t done so lately, mosey on over to twofactorauth.org and see if you are taking full advantage of the strongest available multi-factor authentication option at sites you trust with your data. The beauty of multi-factor is that even if thieves manage to guess or steal your password just because they hacked some Web site, that password will be useless to them unless they can also compromise that second factor — be it your mobile device, phone number, or security key. Not saying these additional security methods aren’t also vulnerable to compromise (they absolutely are), but they’re definitely better than just using a password.






 May marks the third month in a row that Microsoft has pushed out fixes for more than 110 security flaws in its operating system and related software. At least 16 of the bugs are labeled “Critical,” meaning ne’er-do-wells can exploit them to install malware or seize remote control over vulnerable systems with little or no help from users.
May marks the third month in a row that Microsoft has pushed out fixes for more than 110 security flaws in its operating system and related software. At least 16 of the bugs are labeled “Critical,” meaning ne’er-do-wells can exploit them to install malware or seize remote control over vulnerable systems with little or no help from users. Canton, Ohio-based Diebold [
Canton, Ohio-based Diebold [