Conventional wisdom says one reason so many hackers seem to hail from Russia and parts of the former Soviet Union is that these countries have traditionally placed a much greater emphasis than educational institutions in the West on teaching information technology in middle and high schools, and yet they lack a Silicon Valley-like pipeline to help talented IT experts channel their skills into high-paying jobs. This post examines the first part of that assumption by examining a breadth of open-source data.
The supply side of that conventional wisdom seems to be supported by an analysis of educational data from both the U.S. and Russia, which indicates there are several stark and important differences between how American students are taught and tested on IT subjects versus their counterparts in Eastern Europe.

Compared to the United States there are quite a few more high school students in Russia who choose to specialize in information technology subjects. One way to measure this is to look at the number of high school students in the two countries who opt to take the advanced placement exam for computer science.
According to an analysis (PDF) by The College Board, in the ten years between 2005 and 2016 a total of 270,000 high school students in the United States opted to take the national exam in computer science (the “Computer Science Advanced Placement” exam).
Compare that to the numbers from Russia: A 2014 study (PDF) on computer science (called “Informatics” in Russia) by the Perm State National Research University found that roughly 60,000 Russian students register each year to take their nation’s equivalent to the AP exam — known as the “Unified National Examination.” Extrapolating that annual 60,000 number over ten years suggests that more than twice as many people in Russia — 600,000 — have taken the computer science exam at the high school level over the past decade.
In “A National Talent Strategy,” an in-depth analysis from Microsoft Corp. on the outlook for information technology careers, the authors warn that despite its critical and growing importance computer science is taught in only a small minority of U.S. schools. The Microsoft study notes that although there currently are just over 42,000 high schools in the United States, only 2,100 of them were certified to teach the AP computer science course in 2011.
A HEAD START
If more people in Russia than in America decide to take the computer science exam in secondary school, it may be because Russian students are required to study the subject beginning at a much younger age. Russia’s Federal Educational Standards (FES) mandate that informatics be compulsory in middle school, with any school free to choose to include it in their high school curriculum at a basic or advanced level.
“In elementary school, elements of Informatics are taught within the core subjects ‘Mathematics’ and ‘Technology,” the Perm University research paper notes. “Furthermore, each elementary school has the right to make [the] subject “Informatics” part of its curriculum.”
The core components of the FES informatics curriculum for Russian middle schools are the following:
1. Theoretical foundations
2. Principles of computer’s functioning
3. Information technologies
4. Network technologies
5. Algorithmization
6. Languages and methods of programming
7. Modeling
8. Informatics and Society
SECONDARY SCHOOL
There also are stark differences in how computer science/informatics is taught in the two countries, as well as the level of mastery that exam-takers are expected to demonstrate in their respective exams.
Again, drawing from the Perm study on the objectives in Russia’s informatics exam, here’s a rundown of what that exam seeks to test:
Block 1: “Mathematical foundations of Informatics”,
Block 2: “Algorithmization and programming”, and
Block 3: “Information and computer technology.”
The testing materials consist of three parts.
Part 1 is a multiple-choice test with four given options, and it covers all the blocks. Relatively little time is set aside to complete this part.
Part 2 contains a set of tasks of basic, intermediate and advanced levels of complexity. These require brief answers such as a number or a sequence of characteristics.
Part 3 contains a set of tasks of an even higher level of complexity than advanced. These tasks usually involve writing a detailed answer in free form.
According to the Perm study, “in 2012, part 1 contained 13 tasks; Part 2, 15 tasks; and Part 3, 4 tasks. The examination covers the key topics from the Informatics school syllabus. The tasks with detailed answers are the most labor intensive. These include tasks on the analysis of algorithms, drawing up computer programs, among other types. The answers are checked by the experts of regional examination boards based on standard assessment criteria.”
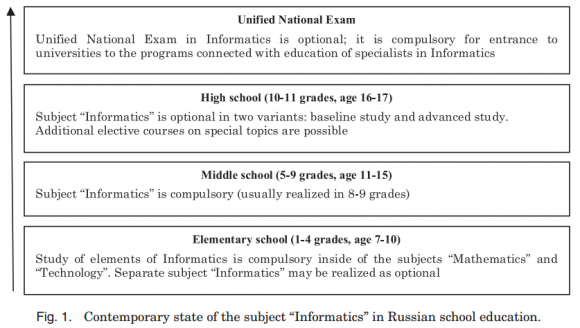
Image: Perm State National Research University, Russia.
In the U.S., the content of the AP computer science exam is spelled out in this College Board document (PDF).
US Test Content Areas:
Computational Thinking Practices (P)
P1: Connecting Computing
P2: Creating Computational Artifacts
P3: Abstracting
P4: Analyzing Problems and Artifacts
P5: Communicating
P6: Collaborating
The Concept Outline:
Big Idea 1: Creativity
Big idea 2: Abstraction
Big Idea 3: Data and Information
Big Idea 4: Algorithms
Big idea 5: Programming
Big idea 6: The Internet
Big idea 7: Global Impact
ADMIRING THE PROBLEM
How do these two tests compare? Alan Paller, director of research for the SANS Institute — an information security education and training organization — says topics 2, 3, 4 and 6 in the Russian informatics curriculum above are the “basics” on which cybersecurity skills can be built, and they are present beginning in middle school for all Russian students.
“Very few middle schools teach this in the United States,” Paller said. “We don’t teach these topics in general and we definitely don’t test them. The Russians do and they’ve been doing this for the past 30 years. Which country will produce the most skilled cybersecurity people?”
Paller said the Russian curriculum virtually ensures kids have far more hands-on experience with computer programming and problem solving. For example, in the American AP test no programming language is specified and the learning objectives are:
“How are programs developed to help people and organizations?”
“How are programs used for creative expression?”
“How do computer programs implement algorithms?”
“How does abstraction make the development of computer programs possible?”
“How do people develop and test computer programs?”
“Which mathematical and logical concepts are fundamental to programming?”
“Notice there is almost no need to learn to program — I think they have to write one program (in collaboration with other students),” Paller wrote in an email to KrebsOnSecurity. “It’s like they’re teaching kids to admire it without learning to do it. The main reason that cyber education fails is that much of the time the students come out of school with almost no usable skills.”
THE WAY FORWARD
On the bright side, there are signs that computer science is becoming a more popular focus for U.S. high school students. According to the latest AP Test report (PDF) from the College Board, almost 58,000 Americans took the AP exam in computer science last year — up from 49,000 in 2015.
However, computer science still is far less popular than most other AP test subjects in the United States. More than a half million students opted for the English AP exam in 2016; 405,000 took English literature; almost 283,000 took AP government, while some 159,000 students went for an AP test called “Human Geography.”
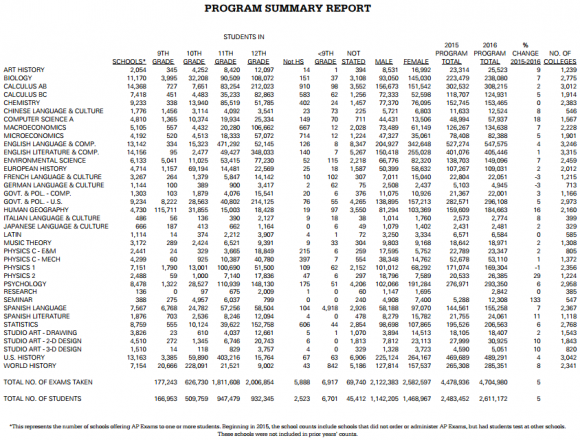
A breakdown of subject specialization in the 2016 v. 2015 AP tests in the United States. Source: The College Board.
This is not particularly good news given the dearth of qualified cybersecurity professionals available to employers. ISACA, a non-profit information security advocacy group, estimates there will be a global shortage of two million cyber security professionals by 2019. A report from Frost & Sullivan and (ISC)2 prognosticates there will be more than 1.5 million cybersecurity jobs unfilled by 2020.
The IT recruitment problem is especially acute for companies in the United States. Unable to find enough qualified cybersecurity professionals to hire here in the U.S., companies increasingly are counting on hiring foreigners who have the skills they’re seeking. However, the Trump administration in April ordered a full review of the country’s high-skilled immigration visa program, a step that many believe could produce new rules to clamp down on companies that hire foreigners instead of Americans.
Some of Silicon Valley’s biggest players are urging policymakers to adopt a more forward-looking strategy to solving the skills gap crisis domestically. In its National Talent Strategy report (PDF), Microsoft said it spends 83 percent of its worldwide R&D budget in the United States.
“But companies across our industry cannot continue to focus R&D jobs in this country if we cannot fill them here,” reads the Microsoft report. “Unless the situation changes, there is a growing probability that unfilled jobs will migrate over time to countries that graduate larger numbers of individuals with the STEM backgrounds that the global economy so clearly needs.”
Microsoft is urging U.S. policymakers to adopt a nationwide program to strengthen K-12 STEM education by recruiting and training more teachers to teach it. The software giant also says states should be given more funding to broaden access to computer science in high school, and that computer science learning needs to start much earlier for U.S. students.
“In the short-term this represents an unrealized opportunity for American job growth,” Microsoft warned. “In the longer term this may spur the development of economic competition in a field that the United States pioneered.”




 The reader — Cedric (he asked to keep his last name out of this story) had grown increasingly aggravated with the calls as well, until one day he opted to play along by telling a white lie to the automated voice response system that called him: Yes, he said, yes he definitely was interested in credit repair services.
The reader — Cedric (he asked to keep his last name out of this story) had grown increasingly aggravated with the calls as well, until one day he opted to play along by telling a white lie to the automated voice response system that called him: Yes, he said, yes he definitely was interested in credit repair services.