Crooks Use Hacked Routers to Aid Cyberheists
lundi 29 juin 2015 à 16:30Cybercriminals have long relied on compromised Web sites to host malicious software for use in drive-by download attacks, but at least one crime gang is taking it a step further: New research shows that crooks spreading the Dyre malware for use in cyberheists are leveraging hacked wireless routers to deliver their password-stealing crimeware.
Dyre (a.k.a. “Dyreza”) is generally installed by a downloader Trojan that is flagged by most tools under the name “Upatre.” The latter is most often delivered via malicious e-mails containing a link which directs unsuspecting users to servers hosting malicious javascript or a basic redirection to a malicious payload. If the user clicks the malicious link, it may serve a bogus file — such as an invoice or bank statement — that if extracted and opened reaches out to an Upatre control server to download Dyre.
According to a recent in-depth report from Symantec, Dyre is a highly developed piece of malware, capable of hijacking all three major web browsers and intercepting internet banking sessions in order to harvest the victim’s credentials and send them to the attackers. Dyre is often used to download additional malware on to the victim’s computer, and in many cases the victim machine is added to a botnet which is then used to send out thousands of spam emails in order to spread the threat.
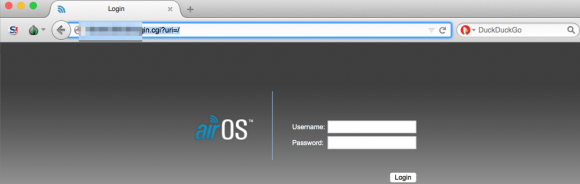
Recently, researchers at the Fujitsu Security Operations Center in Warrington, UK began tracking Upatre being served from hundreds of compromised home routers — particularly routers powered by MikroTik and Ubiquiti’s AirOS.
“We have seen literally hundreds of wireless access points, and routers connected in relation to this botnet, usually AirOS,” said Bryan Campbell, lead threat intelligence analyst at Fujitsu. “The consistency in which the botnet is communicating with compromised routers in relation to both distribution and communication leads us to believe known vulnerabilities are being exploited in the firmware which allows this to occur.”
Campbell said it’s not clear why so many routers appear to be implicated in the botnet. Perhaps the attackers are merely exploiting routers with default credentials (e.g., “ubnt” for both username and password on most Ubiquiti AirOS routers). Fujitsu also found a disturbing number of the systems in the botnet had the port for telnet connections wide open.
In January 2015, KrebsOnSecurity broke the news that the botnet used to attack and briefly knock offline Microsoft’s Xbox and Sony Playstation’s networks relied entirely on hacked routers, all of which appeared to have been compromised remotely via telnet.
Whether you use a router from Ubiquiti or any other manufacturer, if you haven’t changed the default credentials on the device, it’s time to take care of that. If you don’t know whether you’ve changed the default administrative credentials for your wired or wireless router, you probably haven’t. Pop on over to routerpasswords.com and look up the make and model of your router.
To see whether your credentials are the default, you’ll need to open up a browser and enter the numeric address of your router’s administration page. For most routers, this will be 192.168.1.1 or 192.168.0.1. This page lists the default internal address for most routers. If you have no luck there, here’s a decent tutorial that should help most users find this address. And check out my Tools for a Safer PC primer for more tips on how to beef up the security of your router and your Web browser.